Configuration of iptables - Firewall in Linux
What is a firewall?
The first thing to consider when setting up a firewall, is whether it is really necessary, many people today are connected to the Internet in one way or another, from businesses, homes or from a cybercafe, however, few of these people really understand the consequences of opening their computer systems to the Internet.A firewall is typically a software or hardware, through which we connect to a network such as the Internet, and serves as a filter over the traffic that passes through it in both directions, and that at a given moment can reject some traffic in one of the directions.
That means that a firewall, we can detect unwanted traffic to our systems, and in general, possible attacks that we object. In this way, we can isolate our external network devices, allowing our use of the Internet so absolutely normal while minimizing as far as possible the probability of suffering the consequences of an attack.
It is also often needed to expose some Internet server (such as a web server, a mail server, etc ...), and in those cases in principle obviously must accept any connection to them.

Iptables (Free Software)
Iptables is the tool that allows us to set the rules of packet filtering system of the Linux kernel since version 2.4 (in 2.2 was ipchains). With this tool, we can create our firewall tailored to our needs.
These actions are reflected in what are called targets, indicating what to do with the packet. The most used are quite explicit: ACCEPT, DROP and REJECT. As for the packet, the total packet filtering system kernel is divided into three tables, each with several chains which may belong to a packet, as follows.
*FILTER: Default table, for packages that relate to our machine
INPUT: packets received for our system
FORWARD: Packets routed through our system
OUTPUT: Packets generated in our system and are sent
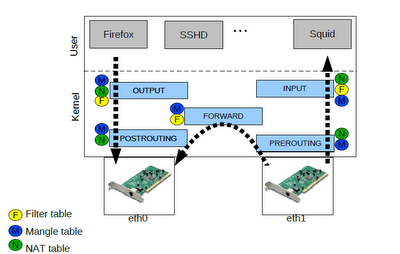
*NAT: Table refers to routed packets on a system with Masquerading
PREROUTING: To alter packets as they enter
OUTPUT: For altering locally generated packets before being routed
POSTROUTING: To alter packets as they are about to exit
*MANGLE: To make special changes to packages more.
PREROUTING: To alter the incoming packets before being routed
OUTPUT: For altering locally generated packets before routing
Specification of rules
Is done with the following parameters (specifying those needed):*-p [protocol]: protocol to which the packet belongs.
*-s [Origin]: packet source address can be a host name, a normal IP address, or a network address (with mask, so address / mask).
*-d [destination]: Like the above, it can be a host name, network address or unique IP address.
*-i [interface-entry]: Specifying the interface through which the packet is received.
*-o [O Interface]: Interface for which you will send the package.
*[!]-F: Specifies that the rule refers to second and further fragments of a fragmented packet. If preempts!, Refers only to the first package, or unfragmented packets.
And also, one that will allow us to choose what we do with the package:
*-j [target]: Allows you to choose the target to which to send the packet, that is, the action to perform with him.
Before starting with the example of firewall rules is important to recognize that the order of the rules is crucial. Normally when deciding which is made with a package will compare with each firewall rule until it finds one that is affected (match), and becomes the dictates this rule (Accept or Deny), ie once a packet matches a rule not analyzed as follows.

Example iptables rules, Initialize
Set default policies, important to define in principle that everything that enters and exits through the firewall only accept and deny what is said explicitly. This greatly facilitates the management of the firewall, and we just have to worry about protecting those ports or addresses that we know we are interested. However this can be dangerous.
echo 1 > /proc/sys/net/ipv4/ip_forward iptables -X iptables -F iptables -Z iptables -t nat -F iptables -P INPUT ACCEPT iptables -P OUTPUT ACCEPT iptables -P FORWARD ACCEPT iptables -t nat -P PREROUTING ACCEPT #iptables -t nat -P FORWARD ACCEPT iptables -t nat -P POSTROUTING ACCEPT
Establish policies to deny access to ssh on interfaces eth0 and 192.168.1.0 network, allowing full access to the network from the network address 172.16.2.0 and 172.16.20.0; also permit 172.16.10.0 network users, can Internet access
Example of rules for the filter table
iptables -A INPUT -i eth0 -p tcp --dport 22 -j DROP iptables -A INPUT -s 192.168.1.0/24 -p tcp --dport 22 -j DROP # iptables -A INPUT -s 172.16.2.0/24 -j ACCEPT iptables -A INPUT -s 172.16.20.0/24 -j ACCEPT iptables -A FORWARD -s 192.168.10.0/24 -i eth1 -p tcp --dport 80 -j ACCEPT
Through this rule is indicating that all traffic from the 192.168.1.0 network, will be masked by the IP address of the network card eth0 (172.16.2.13, for this example)
Example of rules for the NAT table
iptables -t nat -A POSTROUTING -s 192.168.1.0/24 -o eth0 -j MASQUERADE
Note: If the router does not have a configured NAT rule that says make the network 172.16.10.0, it will be essential to establish a rule like this, but this hid the traffic that comes from this network.
iptables -t nat -A POSTROUTING -s 172.16.10.0/24 -o eth0 -j MASQUERADE
This is a small example of iptables, but iptables is a very powerful tool and is useful to perform an unlimited number of restrictions as needed, some prefer early iptables setup a much stronger, initializing the DROP rules, this will require more knowledge by the network administrator.
0 Comments:
Post a Comment