VLANs and 802.1q support on OpenSuse Linux
This week, a friend looked at me as I could do to solve a problem with a Linux server with a single network card and wanted to configure squid, dns, dhcp and apache. The problem is that before I had done with a server with two network interfaces.
Well here is a possible solution to this problem, mainly because his work has a managed switch and can make use of this resource. With this, the configuration will be conducting a linux server with support for VLANs and specifically support IEEE 802.1q protocol.
The graph below shows the traditional pattern they had before the server is damaged. With a public interface and one connected to the private network.
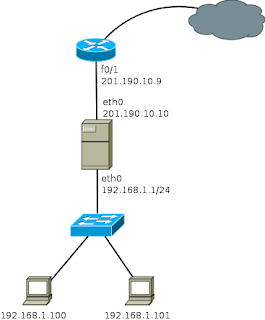
Note: The IP address 201.190.10.9 is invented.
In this scheme, all computers could connect to the Internet through this proxy server.
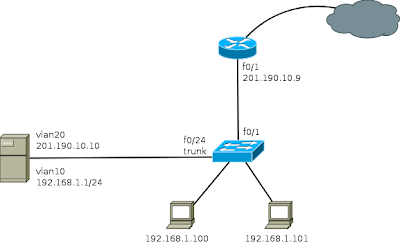
Now we see the same process to set up a server that has a single network card. For this, you must configure a couple VLANs on the switch (as an example I use a Cisco 2960) although this can be done with any switch that has vlan support.
Creating VLANs 10 and 20 (VLAN 10 is used for the network that connects to the Internet and VLAN 20 to the local network)
You also need to configure a port as a trunk, wherein the card that has the Linux server will connect.
Well this is all there is to do in the Cisco 2960, now only need perform configurations on the Linux server, in case I will use a computer with OpenSuse 11.3.
The first thing to do is to install the package "vlan - 802.1q VLAN Implementation for Linux"
Then you can run the following commands:
# Creating the vlan
# Assigning IP to VLANs
As mentioned earlier, it is essential that the port where the server is connected, it is set to port truncal (trunk) on the switch. If the switch does not automatically add the VLANs on the trunk port, you must specify the VLAN 20 and VLAN 10 are allowed on the port.
The other way to set this is the creation of ifcg-vlan10 and ifcg-VLAN20 files with the following content:
ifcg-vlan10 file
----------------------------------
ifcg-vlan20 file
----------------------------------
Once configured, it is necessary to perform a reset of the network with /etc/init.d/network restart command
After completing these steps, running the ifconfig command, network interfaces created appear and can be used in the same manner as in a server with two network interfaces. That is, the steps to configure squid, dns, dhcp, etc, is done in the same manner as in the traditional scheme.
Well here is a possible solution to this problem, mainly because his work has a managed switch and can make use of this resource. With this, the configuration will be conducting a linux server with support for VLANs and specifically support IEEE 802.1q protocol.
The graph below shows the traditional pattern they had before the server is damaged. With a public interface and one connected to the private network.

Note: The IP address 201.190.10.9 is invented.
In this scheme, all computers could connect to the Internet through this proxy server.
Now we see the same process to set up a server that has a single network card. For this, you must configure a couple VLANs on the switch (as an example I use a Cisco 2960) although this can be done with any switch that has vlan support.
Switch>enable Switch# Switch#configure terminal Enter configuration commands, one per line. End with CNTL/Z.
Creating VLANs 10 and 20 (VLAN 10 is used for the network that connects to the Internet and VLAN 20 to the local network)
Switch(config)#vlan 20 Switch(config-vlan)#name internet Switch(config-vlan)#end Switch(config)#vlan 10 Switch(config-vlan)#name local-network Switch(config-vlan)#end
You also need to configure a port as a trunk, wherein the card that has the Linux server will connect.
Switch(config)#interface fastethernet0/1 Switch(config-if)#switchport access vlan 20 (This port connects the wire coming from Internet) Switch(config)#interface fastethernet0/24 Switch(config-if)#switchport mode trunk Switch(config)#do write
Well this is all there is to do in the Cisco 2960, now only need perform configurations on the Linux server, in case I will use a computer with OpenSuse 11.3.

The first thing to do is to install the package "vlan - 802.1q VLAN Implementation for Linux"
Then you can run the following commands:
# Creating the vlan
vconfig add eth0 20 vconfig add eth0 10
# Assigning IP to VLANs
ifconfig eth0.20 201.190.10.10 netmask 255.255.255.0 ifconfig eth0.10 192.168.1.1 netmask 255.255.255.0
As mentioned earlier, it is essential that the port where the server is connected, it is set to port truncal (trunk) on the switch. If the switch does not automatically add the VLANs on the trunk port, you must specify the VLAN 20 and VLAN 10 are allowed on the port.
The other way to set this is the creation of ifcg-vlan10 and ifcg-VLAN20 files with the following content:
ifcg-vlan10 file
----------------------------------
BOOTPROTO='static' BROADCAST='' ETHERDEVICE='eth0' ETHTOOL_OPTIONS='' IPADDR='192.168.1.1/24' MTU='' NAME='' NETWORK='' REMOTE_IPADDR='' STARTMODE='auto' USERCONTROL='no' PREFIXLEN='24'
ifcg-vlan20 file
----------------------------------
BOOTPROTO='static' BROADCAST='' ETHERDEVICE='eth0' ETHTOOL_OPTIONS='' IPADDR='201.190.10.10/24' MTU='' NAME='' NETWORK='' REMOTE_IPADDR='' STARTMODE='auto' USERCONTROL='no' PREFIXLEN='24'
Once configured, it is necessary to perform a reset of the network with /etc/init.d/network restart command
After completing these steps, running the ifconfig command, network interfaces created appear and can be used in the same manner as in a server with two network interfaces. That is, the steps to configure squid, dns, dhcp, etc, is done in the same manner as in the traditional scheme.
0 Comments:
Post a Comment